Blog, Page 1
December 1, 2025
Recent advances in AI based tools have led to three game changing improvements in video surveillance security systems. Detection and Deterrence The vast majority of users look at recorded video…
February 17, 2024
Transition Access Control Proximity / Legacy Technology to High Frequency Credentials The vulnerability of Proximity type card access credentials has been known for several years now. Proximity credentials are easily…
October 24, 2022
Cards and readers have come a long way since they were first introduced to the market. Despite the growing availability of newer and more secure options, many organizations are still…
May 21, 2019
1MP, 2MP, 5MP, 4k ……. which cameras do you need for your video surveillance system? Of course, the answer depends on the situation needs and is influenced by multiple factors….
February 7, 2019
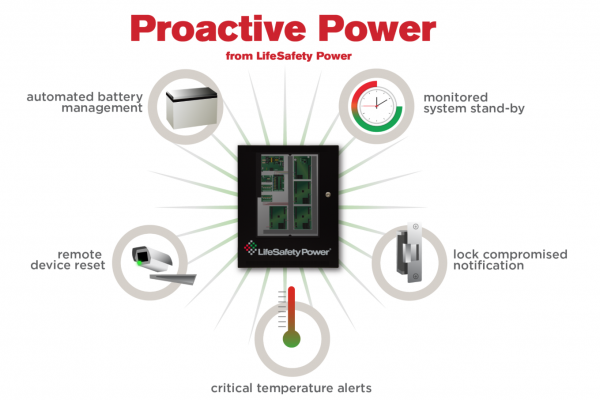
Facilities that rely on access control, CCTV surveillance, and other security systems often overlook a piece of their system that can shut down the entire system if it isn’t properly…
December 1, 2018
Offices, manufacturing facilities, schools, universities, and multi-tenant residences have been transitioning from their loaded key-ring to a more secure and convenient form of door access control: integrated electronic locks. New…
November 1, 2018
Consider how keys and other valuable assets in your organization are stored and managed. Sadly, many organizations don’t have a manageable method of tracking the location and use of valued…
August 15, 2018
In the category of “if I had a nickel for every time …”, camera and video system vulnerabilities would rank right at the top. Nearly every time we are requested…
June 12, 2018
Some type of access control system is just about standard today in schools, manufacturing, healthcare, and local government facilities. Access control protects your employees, your property, and information stored inside….
March 1, 2018
Fire safety is essential – nobody doubts this. Some people believe that a well-designed system straight from the manufacturer is sufficient, but unfortunately, it is not. Commercial fire alarm systems…